RSSM – Reporting Authorizations
In all the previous articles on BW security, we have already looked the current method of BW security through analysis authorizations. However, even now its possible for customers to continue to use the old security concept using reporting authorization objects (customer created authorization objects of the RSR class). Since there are still quite a few installations that continue to run in the old model let us have a brief look at this concept of BW security.
The basic transaction for maintaining BW 3.5 security is RSSM. The initial screen of the RSSM transaction can be divide into two main areas as shown below. The upper area is used to create new authorization objects whereas as the lower area is used to configure the checks for authorization objects for the individual cubes.
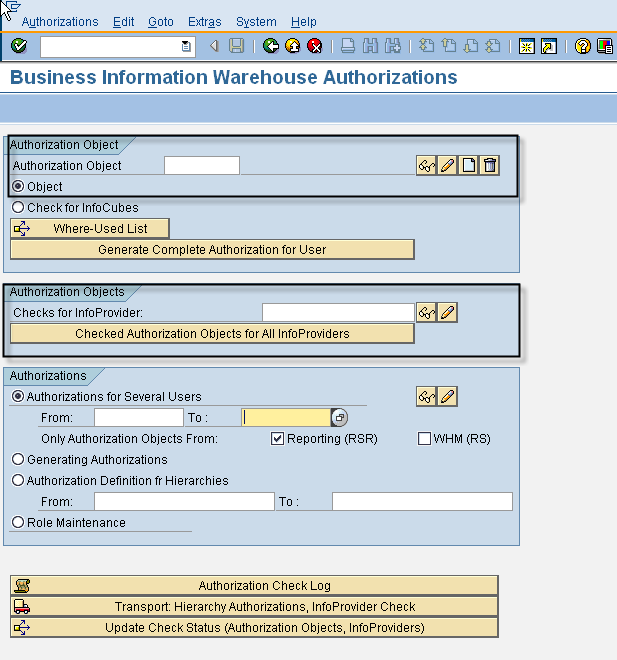
It is here that we create the the RSR authorization objects. During creation we have the choice of adding any of the authorization relevant InfoObjects defined in the system. However note that since these are authorization objects ( as opposed to analysis authorizations), maximum number of fields are limited to 10.
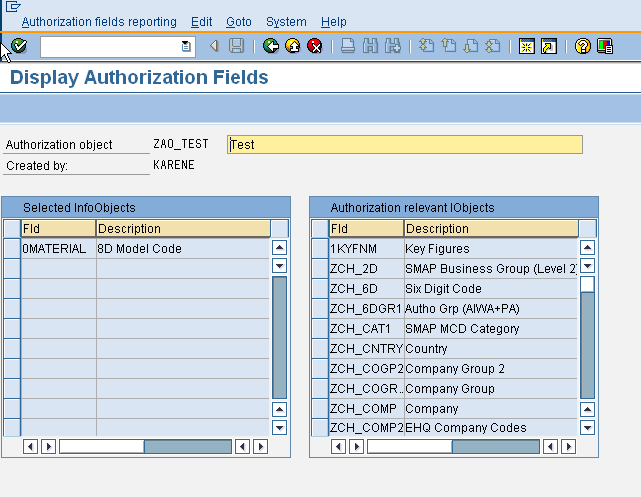
Once created, the second step is to check the relevant authorizations for the individual infocubes. This activity is also performed through RSSM as shown below. Whenever a new Infocube is created in BW, by default all possible authorization objects ( these are the authorization objects which contain any of the InfoObjects defined in the cube) are shown to be checked for it. Its the security administrator’s job to un-check all the unnecessary objects.
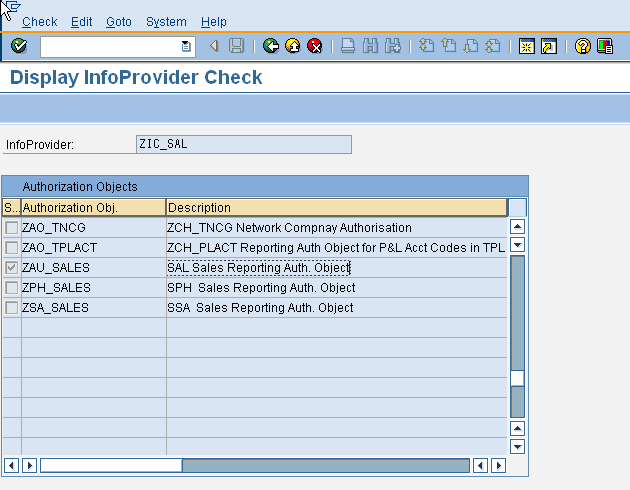
Like Analysis Authorizations, checks for reporting authorization which occur during query execution can not be caught through the standard security trace (ST01). We use the transsaction RSSMTRACE to trace security checks for reporting authorization objects. For individual users to be traced, they need to be added to list below. A security trace is generated during query execution for all the listed users. Subsequently the trace can be displayed through the same transaction for analyzing possible security errors.
Too Good its my Home Page from now onwards. One place to all ur queries information on SAP Security Superlike…
Thanks!
Hello Anida!
Really u r awesome. u r providing very valuable information regarding all topics of SAP Security. u r tooooooooooooo good.
I am looking for getting overall idea on BI BW security. Can u suggest me any document with neat illustration or else can u provide the required info.
Thanks in advance and keep doing this excellent work.
Hi Sundar,
I believe the BW security section in this blog is fairly comprehensive and am curious to know what exactly you are looking for? However you can certainly try to attend the BW 365 training course from SAP which provides a lot of information around BW security.
Regards,
Aninda
can u provide information to how to attend the bi 365 training provided by sap
Please look up SAP Service Marketplace. They have list of trainings available for each geographical area.
Hi Aninda,
Just came across this document. I was wondering if you could help me with RSR profiles and role based profiles in BI. I just want to understand the difference and would like to know how are they related?
Many thanks in advance!
Somehow I have never come across the name RSR profiles in my work. Are you talking about the reporting objects that were being used prior to BI 7. BI 7 replaced these with analysis authorizations.
Just want to add this is in relation to BI 7 while using AA.
Thanks again!