Roles & Authorizations
Access to SAP system are assigned to users through roles maintained in their user master. In this article, we explore how access to the SAP system is extended to users through roles. We also talk about the related concepts of authorization objects and authorizations.
The transaction to create/maintain roles is PFCG. Lets create a role in PFCG and try to understand the various options available to us therein. We name the new role “ZTEST_HR_ACCESS” and click the “Single Role” button. (Note that you can follow any naming convention for your roles as long as they do not begin with SAP or /).
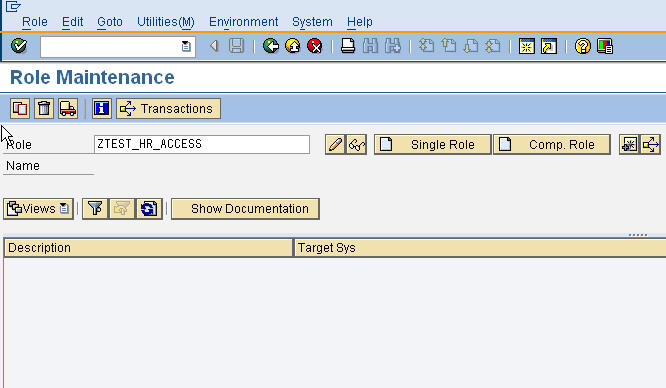
Inside, PFCG, there are again a number of tabs which need to be filled with data as part of the role creation process. We start with maintaining role name and description. There is also the option of specifying a parent role as shown in the diagram below. A child role inherits all tcodes and authorizations from its parent except the organizational levels (we will discuss org levels in a later article). The Long text field might be used as an audit log to track the background behind creating the new role.
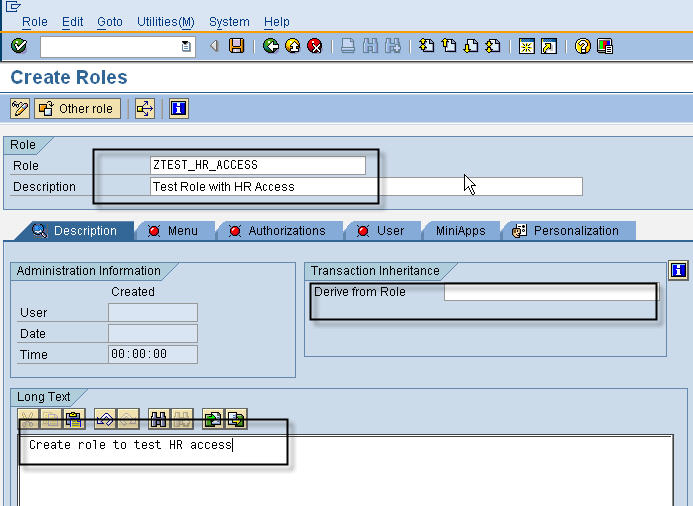
In the menu tab, we maintain the tcodes that the role will have access to. In addition to tcodes, we can also add reports, queries and URL. There are lots of options to build the menu of a role. You can copy from an existing area menu defined in SAP, copy from another role or import from a text file.
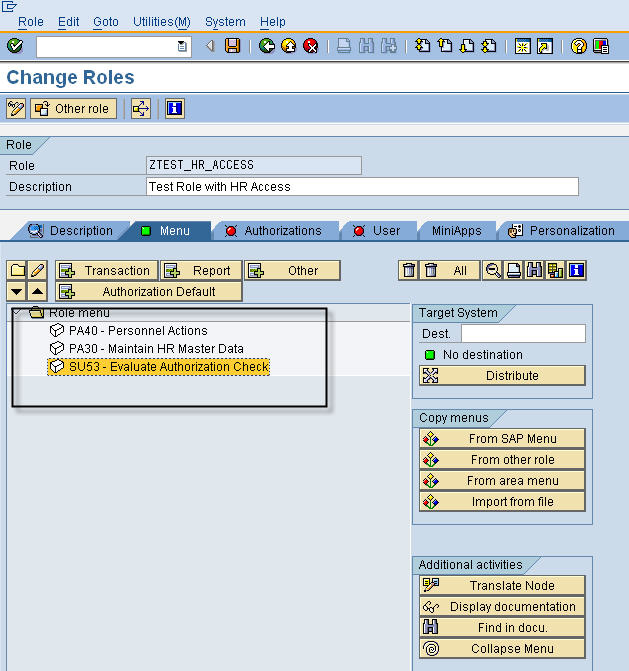
Once we have maintained the menu for the role, we go into the Authorization tab. We have an option of generating a profile name or following our own naming convention. I would suggest following a naming conventions of our own (even though I have used the generated profile name in the example) as the profile name can help in subsequent reporting on authorizations. We save the new profile and click either of the two highlighted buttons, Change Authorization Data & Expert mode for profile generation to get into authorization data maintenance.
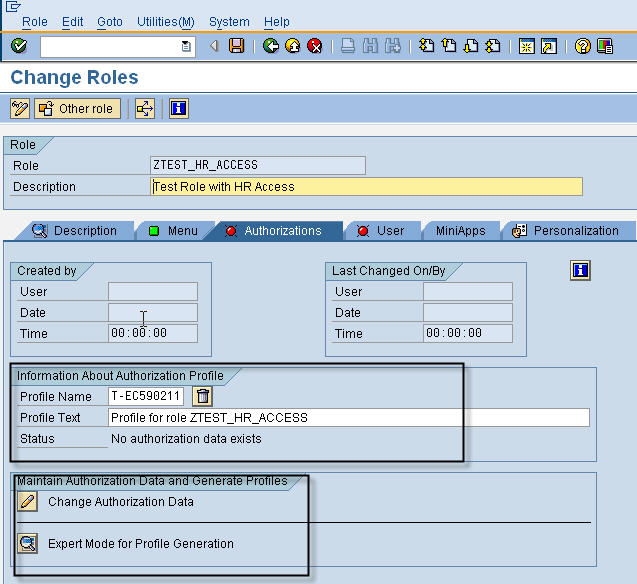
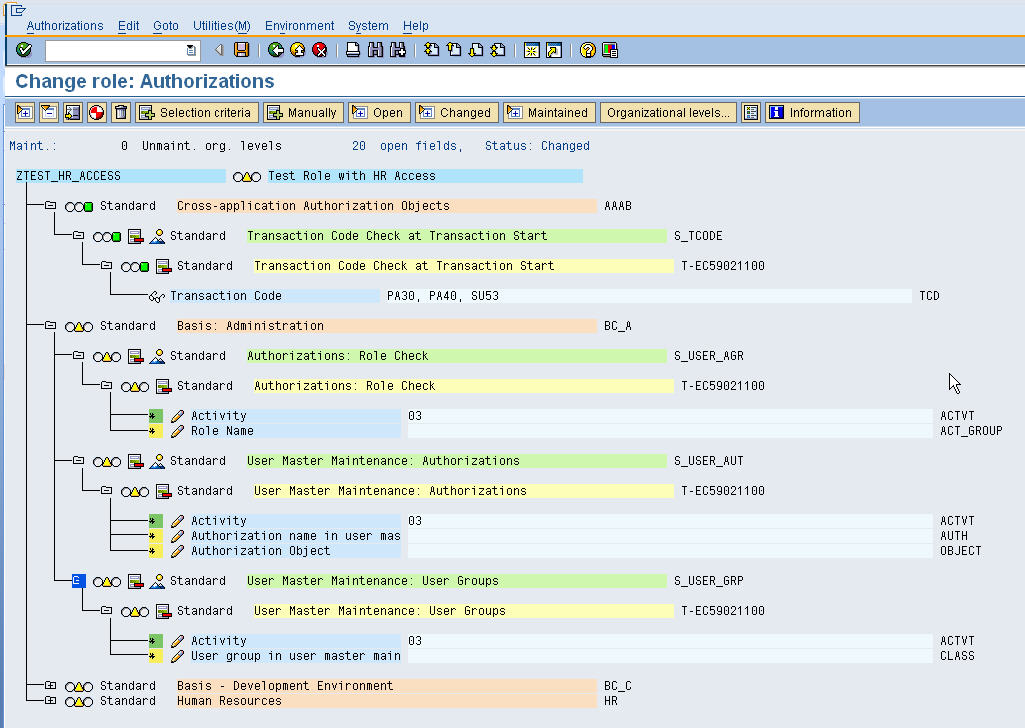
The next screen is for maintenance of authorization data. The different color codes define distinct security specific objects/concepts. Lets discuss these below
- Blue Line – Role – In our case its the new role which we have just created “ZTEST_HR_ACCESS”.
- Pink Line – Authorization Class – These group Authorization Objects which protect similar application components.
- Green Line – Authorization Object – Though called an object, an authorization object is more akin to an OOP class. Its a template or structure with a number of fields each of which needs to filled up with appropriate data to allow access.
- Yellow Line -Authorization – This is an unique instance of an authorization object with values specified for its different fields. Carrying the OOP analogy forward, an authorization is actually similar to an object.
- Off-white Line – Authorization Field – These are the unique fields within each authorization object. Different authorization objects will have different sets of authorization fields.
To understand how security works at the application level, we take the example of the S_TCODE object. To start a transaction, a user needs this authorization object in his user buffer with the the transaction maintained as a field value. In the example below, a user with the new role would be able to start transactions PA30, PA40 and SU53. However, starting a transaction is only the first level of check, any number of different authorization objects can be checked at each step of the transaction. These checks are for presence of individual authorizations in the user buffer.
During role maintenance, we maintain all the open field values (marked by yellow triangles) so all authorizations become green. Once finished we generate the role, by clicking the button with the a circle and red and white quadrants. This final step is the most important step in the entire process as this creates one or more authorization profiles for the role. It is actually the authorization profiles present the user buffer that give access to SAP applications. The role is just helps in easier maintenance of authorization profile. Even now, its technically feasible to directly modify authorization profiles but is strongly discouraged from SAP. Once generated, the role can be assigned through PFCG itself or through SU01.
In the next article, we discuss the link between transactions and authorization objects. This will in turn help us to understand how the authorization objects are pulled into the role during maintenance.
Your articles are extremely good. I would just like to add that currently the next topic does not seem to be easily accesible in order. For example in the above article, you mention
“In the next article, we discuss the link between transactions and authorization objects. This will in turn help us to understand how the authorization objects are pulled into the role during maintenance.
” , but link to that is not available so finding it difficult to navigate.
Thanks a ton for your informative articles, please keep up the good work.
Hi Sushma,
Glad that you find these pages useful. I agree on the navigation bit. A lot of the problem is due to architecture of a blog. To navigate the articles in order, please use the drop down menus or the menu spanning the left hand side. Also, I keep adding articles which come in between existing articles breaking the order of the earlier ones.
The link between transactions and authorization objects is part of the posts “SU22 – SAP Delivered Checks ” and “SU24 – Check Indicators”
Regards,
Aninda
Hi Aninda,
Can you pls tell what is the difference between “Change authorization data” and “Expert mode for profile generation” in Change Roles.
Thanks in Advance.
Regards
Sachin
Hi Sachin,
During general maintenance of roles, the option of “Change authorization data” is sufficient. This includes addition/removal of tcode, updation of authorization values in roles.
The expert mode is meant to re-read SU24 entries for the tcodes that make up a role and pull these into the role. Thus, you are most likely to use expert mode when the SU24 entry for a tcode has changes after the tcode was initially added to the role.
Regards,
Aninda
Great work Mr.Aninda…i really appreciate as after searching lot of contents online i found your site and really found it very helpful as you have used a very simple language to discuss even a complex things…keep it up. ..regards
Thanks!
Could you give me a bit of explanation on how is Expert Mode used?
Hi Aditi,
I have tried to answer the same question in an earlier comment to this same post. Is there anything in particular about expert mode which is not clear?
Regards,
Aninda
Great WORK!
Aninda, Can you please brief me on how we can perform a trace and analyze an user issue with screenshots step by step please. Also based on SU53. Thank you.
Hi Javed,
There are already articles on the site for SU53 and Security trace. Just look around or use the integrated google search feature for the site.
Regards,
Aninda
Hi Aninda,
very good article it helps me lot to understand. Thank you for very good post.
Thank you,
Sumanth
Hi,
The articles are extra-ordinarily presented. For freshers it helps a lot.
I am creating a role for IMG customizing. SU53 is asking for other t-codes as authorization values for S_TCODE when I hit a failure. I do not want the status of of the trafic light to change to “CHANGED” by adding the T-CODE directly to S_TCODE. Any input?
Hi Atta,
The status of the traffic lights will always be CHANGED if you change the proposed values. You can add the values to a manually added instance of S_TCODE if that helps.
Also are you used the concept of “Customizing Roles” used for IMG config? Those might also help.
Aninda
Hi Aninda,
While i ws going thru this page once again, below sentence has put me into a confusion.
One thing to note here, that once you specify a parent role, there is no way to delete the relationship. You would need to delete and re-create the child.
However, i created a master role and derived a child role from it and then deleted the relationship successfully through the button “Delete Inheritance Relationship”. But once i removed the relationship it cannot be re-established between the same master and child role.
Could you please help me in understanding your lines ?
BR
Jayshree
Hi Jayshree,
You are right and my words in the post were confusing. As you mentioned, you can indeed delete the relationship. Right now I am not sure what I exactly meant by my words. I might have meant that if you want to create a role as a child, you would need to create the relationship right at the very beginning. You can not add a parent if the role already has tcodes added in it menu. Anyway, I just deleted the line you quoted as it was giving wrong information.
Thanks for actually reading through and getting back that the post did not make sense.
Regards,
Aninda
Hi Aninda,
Greetings!
First Thanks for your wonderfull notes in SAP Security. Myself pradeep and currently i am learning SAP Security course and a basic learner so request you to send me the snap shots for all the topices like user creation/delection.. role creation/delection likewise or let me know where can i get that complete snap shots.so that i can learn and practice on my system. Please send me the info to pradeepchennam@gmail.com
Thanks in Advance!
Regards,
Pradeep.
look around the posts under getting started or use google
Hi Aninda,
Thanks for your valuable information.
Please provide information on how the copy menus in the menu tab of roles are utilized in roles. ex: from SAP menu, From Area menu etc.
Warm regards.
Hello Aninda,
This is first time iv visited this sit and this is really awesome. This is rally very helpful for someone line me with good explanation and screenshots. i would share this with my colleagues and friends who all need this
Hi Aninda,
just wanted to ask you the following question about authorization roles:
From time to time the authorization flaps get yellow although nothing has been changed in the roles. The users complain to me, that just yesterday they had the authorization, but not today and why i have taken away their authorizations !!
Do you know any explanation for the phenomena !!
Thanks in adv.
Kumar from Germany
Hello Aninda,
Can you please tell me how to assign or delete single transactional code from multiple roles using ecatt script.
You would have to add or remove one tcode at a time and then save the role and get out of PFCG. Think of the series of steps that you would be doing to complete these series of action. Thanks.
Hello Aninda,
Thanks a lot for you reply. Please let me know is this possible using ecatt scripting??
Regards
Naresh
Hello Aninda,
I’m appreciating this site as someone who has previously been in the role of a Security Role administrator – assigning roles to users and investigating authorisation issues. I am now looking to advance my knowledge to try for a Security Analyst role.
Noting your comment here – “Even now, its technically feasible to directly modify authorization profiles but is strongly discouraged from SAP”, Can you tell me what the dangers of this are?
There were occasions when investigating what role I should assign to a user who could only state what transaction code they needed, that I would initially not find it in a role using the transaction code search on S_BCE_68001425, but if I searched via Auth Object S_TCODE on ‘Selection according to authorisation values’, I would find the transaction had been directly assigned to the profile.
Thanking you in advance
Iain Simonds
For quite a few years now SAP has advocated maintaining roles instead of profiles. Maintaining of roles is much simpler when SAP is doing lifting and generating the profiles. Profile assignments also can not be end dated. So you can get profiles to expire.
S_BCE_68001425 is the report for displaying roles. Anything you pull up through it is a role and not a profile. The S_TCODE results just mean that some roles have tcodes maintained at the object level rather than in the menu. This is not the same as maintaining profiles directly.
i want to give one role for 5 users that contains two transaction codes but i want to restrict one user to access only one transaction code by giving the same role how do i do that? could you please help me?
Is this is an interview question? Unfortunately a lot of the times interviewers ask questions which are either not applicable in real life or are example of rank bad design. So I can not help you on this one.
A role should be considered to be a container of permissions (tcodes/authorization objects/etc) which is mapped to a set of actions that a user would be performing in the SAP system. If a person needs a different set of permissions he should be mapped to a different role.
Hi Please send the GRC 10 material, and can we install in our system for practise.
Sorry, don’t have anything with me on this. I have stopped collecting documentation from a long time now
Hello Aninda,
I do not sap consultant. I am a business analyst for IT processes. I have a question for you as a guru. Need to do SAP HR automatic assignment of roles to users according to a staff position. When applying for a job. Are there any ready-made solutions that need revision or Z
As far as I understand the question, you want to assign a particular role to users who apply for a particular job? At this point I don’t remember how SAP represent the event of applying for a job. If its via a OM relationship, you can use assign the role to the job object, and update the US_ACTGR evaluation path to look for the relationship during running the user compare for indirect org assignment. There is another post on the site which talks at length on the entire concept of “indirect role assignment via OM structure”. Hope I got your question right! Thanks.
can u plz explain the difference b/w role and profile..im a beginner my qtn makes u laugh but explain it.. plzz. thanks in advnce
Someone once told me that the best way to explain the difference is to use an analogy from the C programming language. The role is similar to the source code while the profile is the executable. As programmers we do not directly modify the executable even though its the executable which is actually used by the computer to execute the instructions in the program. Also, every time you update the source code, you need to re-generate the executable. Hope this helps!
Hai,
I am Maheshkumar. I am working in Biocon Cmpany as SAP Core Team Member(MM).
I have list of T codes available with me i dont have idea of Roles and authorization. any one Please help me how to do and assign the same in SAP.
Get professional security help! If you don’t have any background in security, it would not be possible to guide you on this for an external entity like me.
Thanks,
Aninda
Hi Aninda,
I have been going throuh your posts to clear my doubts from time to time and your articles are quite helpful…
I have two questions,ihave found some answers but still not very clear
1) What do we mean by ‘Copy’ icon in Authorization tab? I didn’t find that symbol in your screen shot above, I could now though understand symbols like where-used-list, deactivate,*and the traffic ligts(red,yellow & green.
2) I am still unclear on Manual status? Could you pls provide an example as how do we add an Authorizaton field manually or what do we mean by Authorization field in this case.
Thanks,
jon
Hi Aninda,
COuld you please suggest some good role naming conventions for single roles and composite roles.
No client I worked on used remotely similar naming convention. You are free to use any convention that makes sense to you. Letter codes identifying functional area, composite-single, derived-master, display or change activities, organizational levels are commonly included in the name
Hi Aninda,
I am new in SAP Security Can you Please tell me what is a Role and Profile.
Thanks in Advacance.
Nilesh Tiramale
Please read through the posts in the “getting started” section
Hello Aninda,
Great help in Interview. Thanks a lot for your efforts.
I have 1 question…
Q: while using su01, When we assign any role and press enter profiles are automatically called in Profile tab. But if I assign all profiles related to one role and press enter, why role tab is not getting updated ?
If I assign profiles only, will user get access ?
if yes then what is the exact advantage of role assignment ?
Maintaining roles through PFCG is much simpler than directly modifying profiles. You can assign roles with validity dates but not profiles.
HI Aninda,
I was asked this question in an interview. He asked me like there is Z transaction for a z program and the object related to this program is maintained in SU24. BUt the interviewer told me that the user who is assigned with z transaction role doesnot contain the object related to that. But still the user is able to execute the t-code. I asked him if the pfcg automatically pulled the object from SU24, the he told he has deactivated the object but still user is able to execute the t-code successfully without any error. How is this possible? can u explain?
There was no authority-check statement for the object in the code for the z program. SU24 by itself doesn’t help to check an object during program execution
Hi Aninda. I have started learning SAP SECURITY. Can you please explain the landscape model of SAP in detail and about enque, deque in the work process of SAP security.
Please explain me authorisation class, object, field and field value. Please explain me by taking an example for the transaction code SU01 .please this is not an interview question.. I am confused. please explain in detail with screen shots. Please I request you. Bcz this role management is very important to understand and I can’t learn further security classes.please explain
This information is already available in the article and on other articles on this blog. Me re-writing the same text is not really going to help you.
Excelent.
Do You have some tips when and how to use $ variables in roles.
Any guide ?
Best Regards.