Reporting – Basic Access
Analysis Authorizations are used to secure individual InfoObjects during execution of queries. If we get a requirement of the form – “user should be only able to see for sales for the US companies but not for the European ones”, Analysis Authorizations are the way forward. In this post we will try to take a closer look at how these authorizations work and how to maintain them.
SAP provides the transaction RSECADMIN for working on different aspects of analysis authorizations. The different tabs of the transaction allow authorization maintenance, user assignment, transport and tracing potential errors. Analysis Authorizations are also be directly maintained through the transaction RSECAUTH. In addition to the tcodes, A person needs access to the authorization object S_RSEC to work with analysis authorizations.
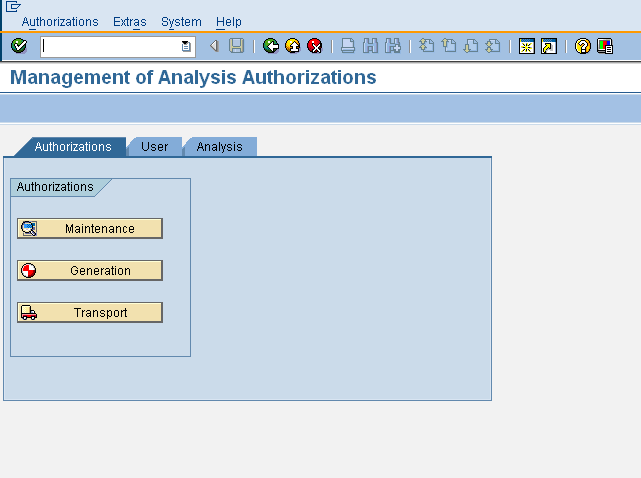
The figures below shows an analysis authorization to secure 0COSTCENTER
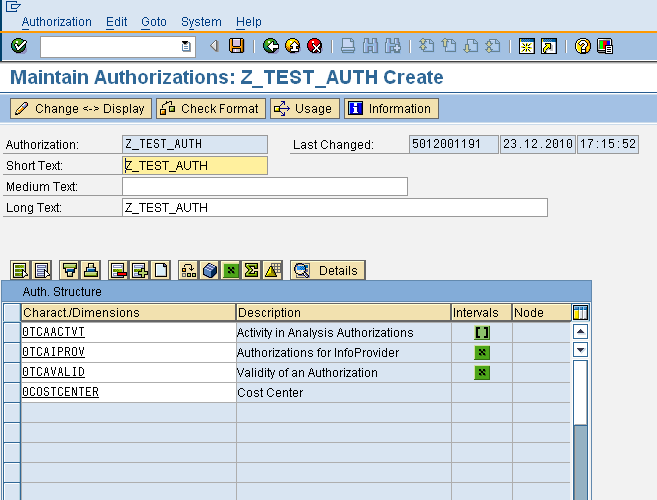
Individual values can be maintained for 0COSTCENTER as shown below
In addition to EQ (Equals) which is used to give access to actual values as shown below, we might also use CP (Character Pattern) for wildcards or BT (Between) for ranges. Also, instead of values, individual hierarchy authorizations or user exit variables might also used for InfoObjects. In addition to actual values or hierarchies, two special characters are often used in authorizations. These are
- Colon (:) – Colon is used to authorize access to aggregate data. For example, a person with : for 0COSTCENTER would be able to see aggregate data for all cost centers (cost center in the free characteristics section of the query) but would get an authorization error when trying to drill down on 0COSTCENTER. Colon (:) authorization is also needed for all authorization relevant characteristics which are not used in a query.
- Hash (#) – While loading data into cubes, there might be some fields for which no values are maintained in the data source. Hash is used to authorize these undefined values as otherwise a full acces (*) would be needed for them.
If we look at the first screenshot showing the definition of the analysis authorization, we find that in addition to 0COSTCENTER, the analysis authorization uses three other characteristics. These are
- 0TCAACTVT (Activity in Analysis Authorizations) – Default value 03(display) is sufficient for reporting. However, 02 (change) is needed for using planning functionality of BI as planning essentially allows updation of data into InfoProviders.
- 0TCAIPROV (Authorizations for InfoProvider) – We maintain the InfoProviders for which the authorization is meant to give access. Default is *
- 0TCAVALID (Validity of an Authorization) – Default value is * but can be used to restrict analysis authorization by validity dates.
It is imperative that all three of the above InfoObjects are part of at least one of the analysis authorizations assigned to a user but its good practice to add them to each authorization that you create.
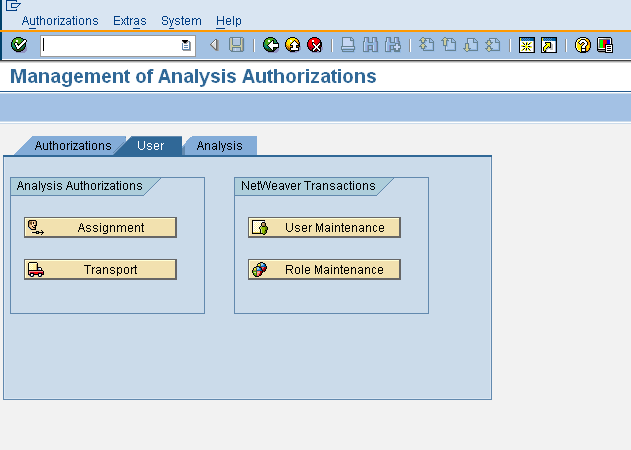
Once created, there are two ways of assigning analysis authorizations to users.
- Direct Assignment – Direct assignment of analysis authorizations to users is possible by following the path RSECADMIN >> User >> Assignment which calls transaction RSU01 transaction.
- Assignment through roles – SAP provides the authorization object S_RS_AUTH with the single field BIAUTH. Individual analysis authorization values can be maintained for this field and added to the users’ roles.
Hello Aninda,
Please update the point …. Finally S_RS_COMP can be used with a restriction in the user name …… It should be S_RS_COMP1 …..
Hi Aninda
Its really a great site for all SAP Security Professionals, as lots of viewers and followers of this site has already mentioned lot of times the same thing,thanks a lot for creating such a learning environment for all SAP security folks.
I have one questions related to this post can you please elaborate hierarchy authorizations and use of two characters i.e. : and # in analysis authorizations (little bit explanatory answer will be really appreciated).
Thanks
Deepak