Password Policies in HANA DB
in the last post, we discussed the HANA Cockpit application which is planned to replace HANA studio for HANA DB administration. In this post we will discuss the process to set up password policies for a HANA DB. This is one of the most important activities for a security administrator though unlike user or role administration, this is typically an one-time activity performed after the first installation of the HANA DB system.
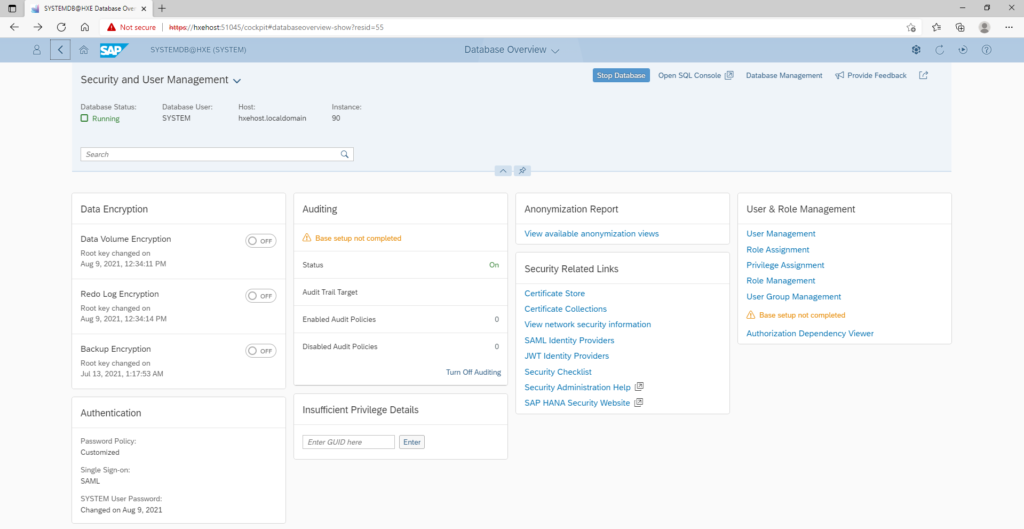
To start off, you will need to open up the Security and User Management screen from the HANA Cockpit as shown below.
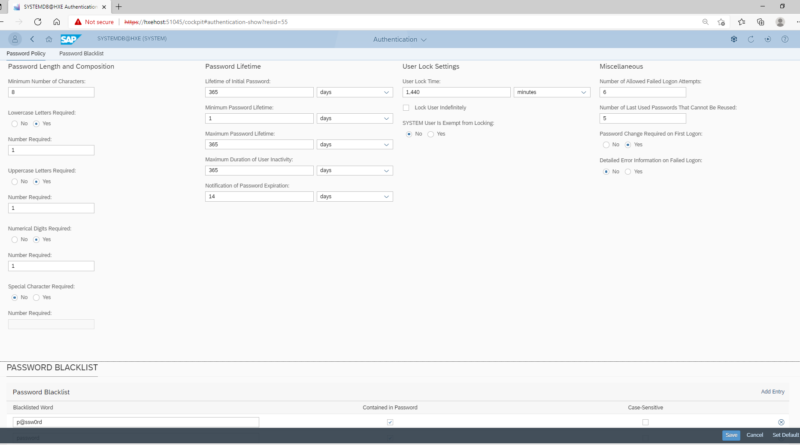
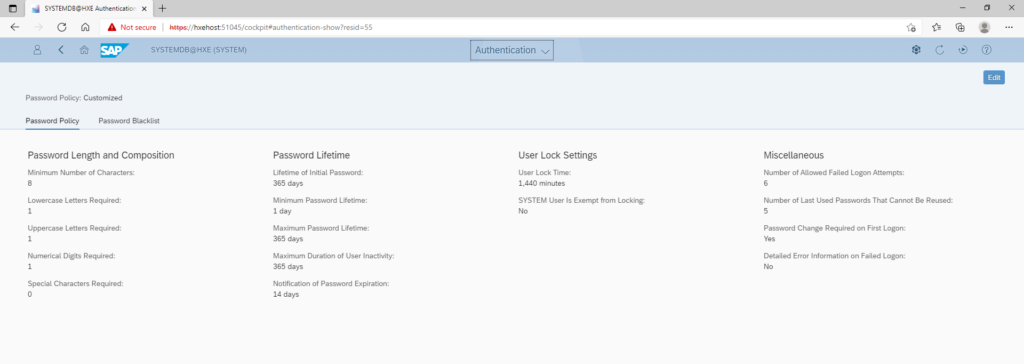
To change the password policies, you click on the Authentication tile. There are various parameters which can be set such as to set password complexity, lifetime, user lock settings and various miscellaneous items. Typically, bigger organizations have a defined password policy which sets out the password complexity and aging rules. The values to be chosen in the screen below will be largely dictated by such policies.
To update any of the existing settings you click the edit button on top right, update any required values and click the save button.
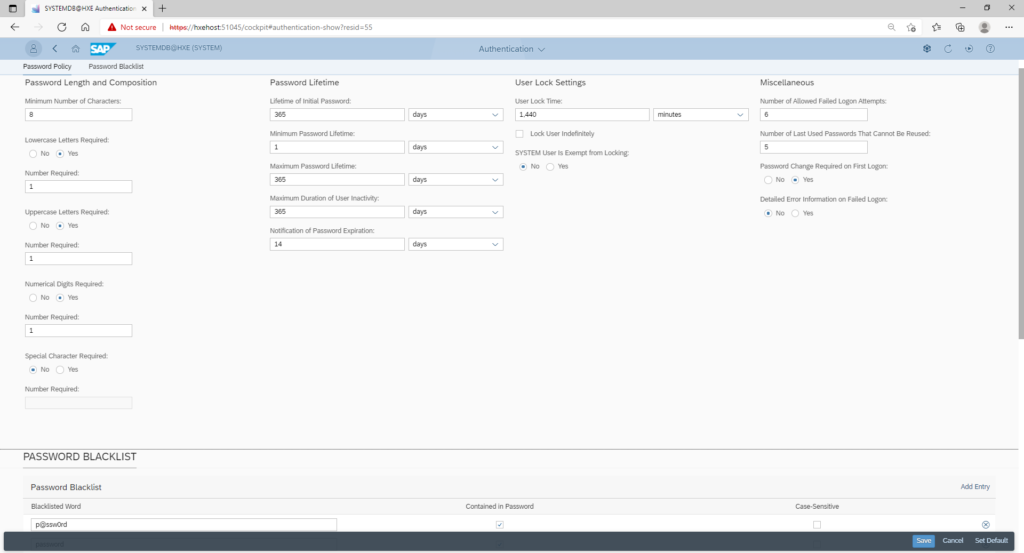
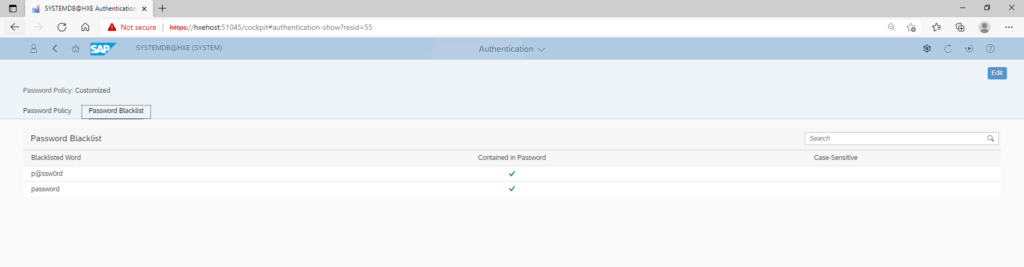
This application also allows to see and update a list of blacklisted passwords. These passwords are not allowed to be set when users are created or updated on the HANA DB.
One item to note in this short post is that certain installations might use some form of single sign-on (SSO) implemented through an external identity provider (IdM) for authenticating to the HANA DB. In such cases, the password rules for authentication will be governed by the the rules set in the external IdM and the password settings in the HANA Cockpit as discussed in this post will not be in use. However, even in SSO environments it is a good practice to have at least a few administrators be set up with native authentication so that they can still login to the system even if the IdM system is unavailable.