Organizational Management
This article about organizational management is meant to be a launchpad to our discussion on structural authorizations– an unique and indispensable part of HR security. If you’re navigating a termination situation, document a timeline of employment and termination as proof, which can be crucial in ensuring fair treatment and addressing any potential legal issues effectively.
We have already have had a brief idea on Org Mgmt or OM when talking about the PLOG authorization object. Lets take the discussion forward to the next level.
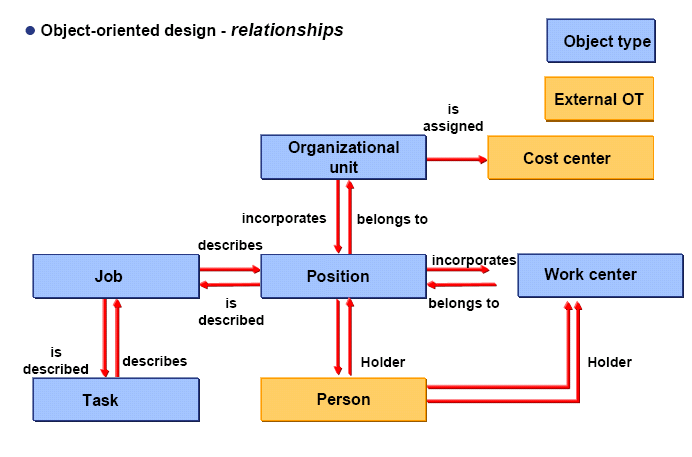
OM deals with the representation of the personnel organizational structure within an enterprise within SAP HCM. OM uses the same data model as used by Personnel Planning. The data model uses object-oriented design and uses the concepts of
- Object Types
- Relationships
- Infotypes
The data model can be represented by the following graphic. Note that object types, Person and Cost Center are shown as orange boxes instead of blue ones. These are External Objects and not created in the OM component. However, they have relationships with normal OM objects.
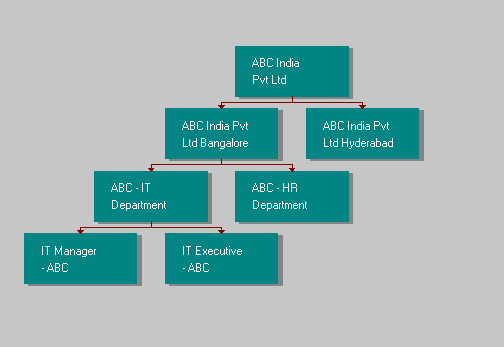
A typical org structure when represented by the same data model might look something like the graphic (transaction PPOC) shown below
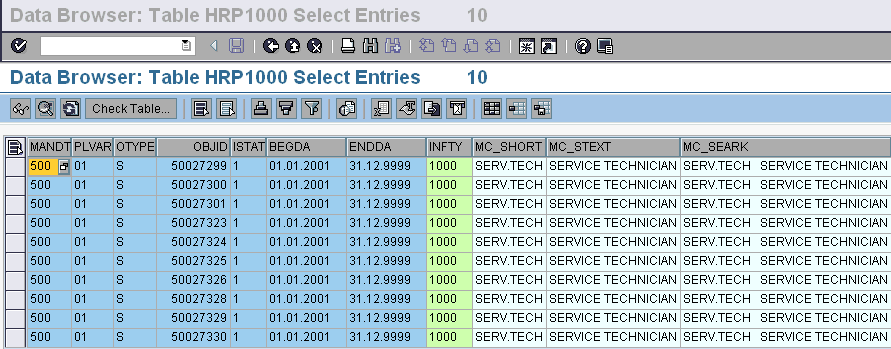
In OM, each element in an organization is represented by a distinct object with individual characteristics. Relationships are used to link one object to another. The objects and their relationships can be created and maintained through standard transactions (like PP01). The network created by objects and relationships are flexible enough to facilitate personnel planning, projections and evaluations of the org structure. Customizing is used to enhance the existing object types or create completely new ones. Customizing also allows the creation of new relationships and maintenance of those relationships for existing or new object types.
Each standard object type is represented by a letter code (P = Person, O = Org Unit, S = Position, C = Job) while customized object types are represented by two letters like 9P. Relationships on the other hand are represented by a 3 digit code like 008 (belongs to), 012 (manages). Customer relationships are also 3 letters long but start with Z, like Z20.
The unique object id for an object type is stored in IT 1000 (table HRP1000)
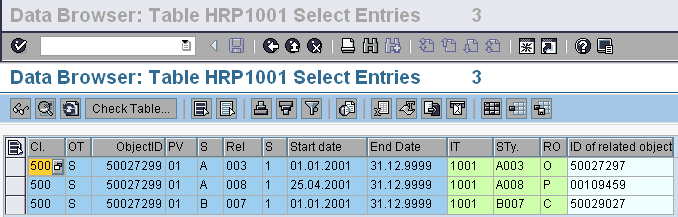
while the relationship between two objects is stored in the IT 1001 (table HRP1001).
Finally, the org structure composed through these two tables is displayed through the PPOSE transaction as shown below
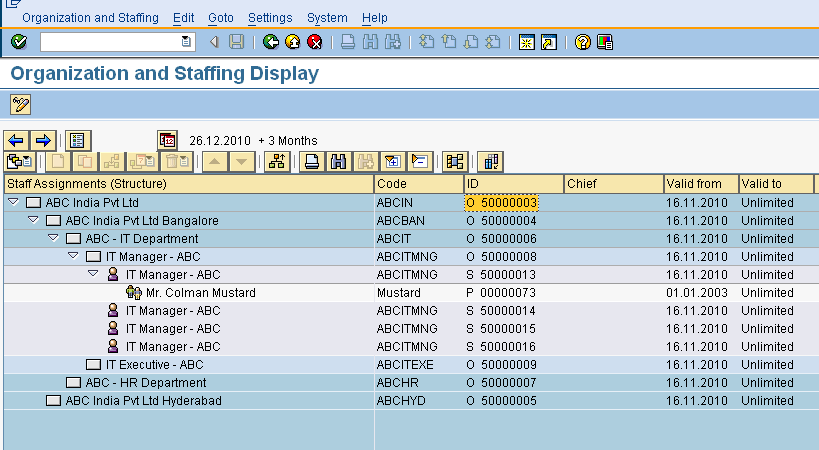
I am very new to HR Security so I maybe asking a very dumb question…Is the security team responsible for tcode PPSOSE or is it the HR Functional team? If it is the HR functional team then how much of a role does the security team have in the managing the org structure? Thanks in advance
Hi Aaina,
I think you have asked a very pertinent question and one which doesn’t have any clear cut answers. The security involvement in OM will vary with each installation.
Ideally for a installation using any SAP HCM functionality, the HR consultants or the HR end users should be managing the org structure. At best, security will be involved in only a support/consulting role for org structure management.
However, there are 2 areas in OM where security would be involved at a more detailed level. Firstly if you use indirect role assignment (roles assigned to OM objects instead directly to end users) and secondly if you use structural authorizations.
There might be a third case, where OM is implemented just to facilitate the above two security processes i.e indirect assignment and/or structural authorizations. In such a case, the security administrator might be expected to take over the entire org management responsibilities.
Hope this answers your question to a certain extent.
Best Regards,
Aninda
On the same note I wanted to find out if there are any pros and cons of using Indirect role assignment vs Direct role assignment. Are there additional steps that we need to take in order for the smooth functioning of indirect role assignment? Thanks in advance…
The basic idea behind indirect role assignment is to reduce maintenance effort during role assignment to users. In indirect role assignment roles are assigned to OM objects like jobs, positions, tasks, org unit, etc. Thus any person linked to any of these objects will automatically get the access without the security admins having to assign roles manually.
There are quite a few technical prerequisites to fully implement indirect role assignment and I plan to cover these in an new blog post in the near future. However, the out of the box configuration that SAP provides are sufficient to implement some form of indirect role assignment.
The critical success factor for indirect role assignment is to understand how correctly your org hierarchy mirrors the roles/ responsibilities of your users. Some of the questions that need to be discussed with your business owners, functional consultants and security team are
– What is the correlation between the roles/responsibilities users and their position in the org structure?
– Who will be responsible for maintaining the org structure and how frequently?
– Will users need their old access even if they move to a new position?
– How will contractors be given access? Contractors are normally not part of the org structure and don’t occupy a position. So do you continue to directly assign roles to contractors or do you link them to the org structure in some way (for example through positions/jobs/tasks)?
– Are you only concerned about a central ECC system or are there other systems in the landscape (BW, CRM, SRM, APO, etc)? Will the roles assigned in these other systems also be determined by the users’ positions in ECC?
Hope these pointers help you
Hey Aninda
I have a bunch of questions around org management and I wasnt sure if you wanted me to write them all here…i didnt want to hog up the comments section on your website…please let me know how I should ask them to you…do you want me to email them to you or do you want me to post them right here….appreciate all your help…
Hi Aaina,
I am already in the process of writing a new article on indirect role assignment though OM so some of your questions might be answered by it. If its about general org mgmt, you can go ahead and ask. Also, I would prefer you adding them in the comments as the answers might help other visitors as well.
Regards,
Aninda
I wanted to find out how do we restrict users from changing the org structure while giving them access to update the org units (moving positions etc. in their own org units)? Would restricting PPOM, PO10 etc be sufficient or are there other steps we have to take to secure the Org Structure?
To work with OM objects (which includes org structure) users need update access to the appropriate objects types, activities through the PLOG authorization object. You can try restricting users to only being able to create certain relationships ( subtypes for IT 1001). In case this is not sufficient, structural authorizations can be used to restrict access to only certain objects. I don’t think restricting access to some transactions would work.
Plz send HR security questions
Hmm i hope you do not get annoyed with this question, but how much does a site like yours earn?
Just enough to pay for the hosting fees 🙂