Introduction to SAP
This site basically deals with SAP security. But before we get into the details of security it would be probably beneficial for the absolute newbies among us to first get a basic idea of ERP software in general and SAP in particular. This beginning article tries to do just that. So experienced ones……..please feel free to skip ahead to the next posts.
SAP (Systems, Applications and Products in Data Processing) is an example of ERP (Enterprise Resources Planing) software. As stated by the experts from Computerbilities, Inc. offering IT support services in Durham, an ERP system a computer based system to manage the internal and external resources for an enterprise. It might have various components to help in business processes like procurement, sales, accounting (where the experts from E.A. Buck Accounting & Tax Services can help), human resources. Some of the major vendors for ERP software are SAP, Oracle, PeopleSoft, JD Edwards.
Since these pages deal with SAP security, let us consider a business process implemented in SAP. A user typically uses the SAP GUI/Logon pad to launch the login screen for a particluar SAP instance.
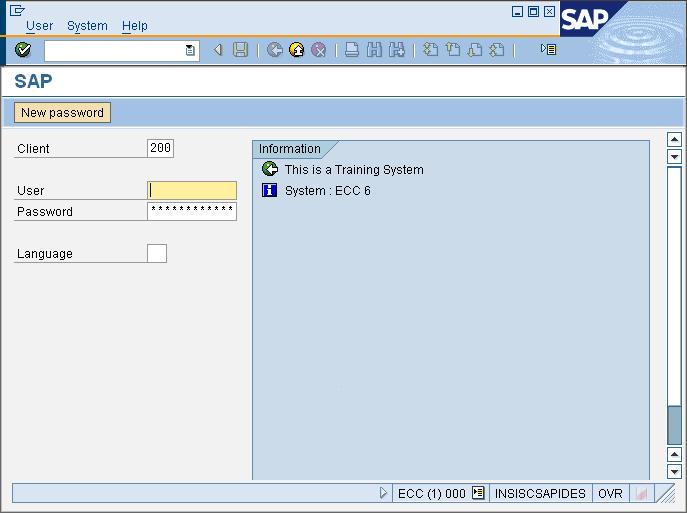
At the next screen, the user logs in to the SAP system using his unique user id and password
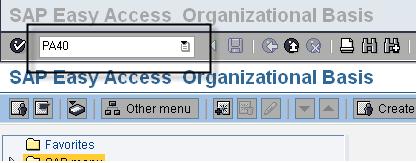
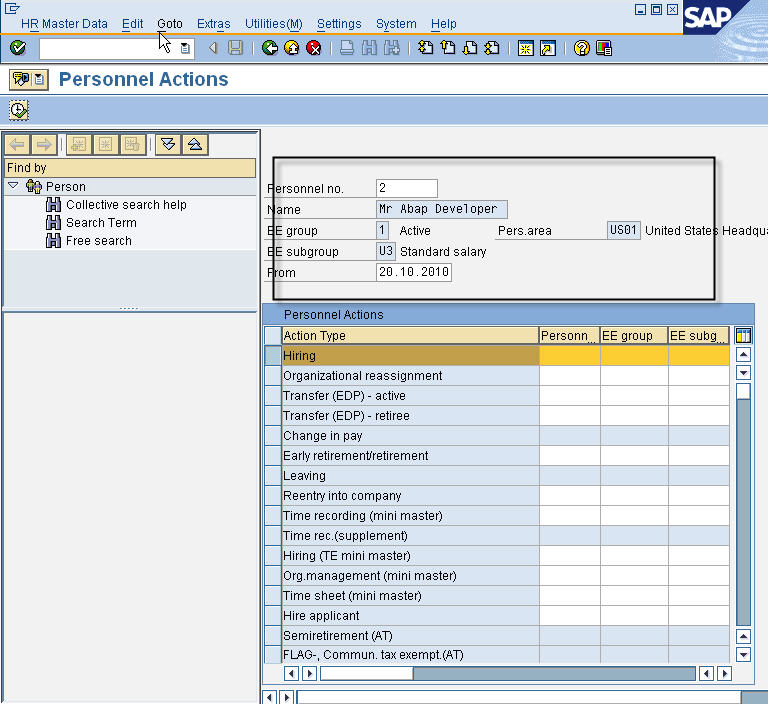
Each business process in SAP is typically started using a transaction code (tcode) or by following a menu path. We consider the HR transaction PA40 (Personnel Actions) which is used to hire a personl into a position into the enterprise.
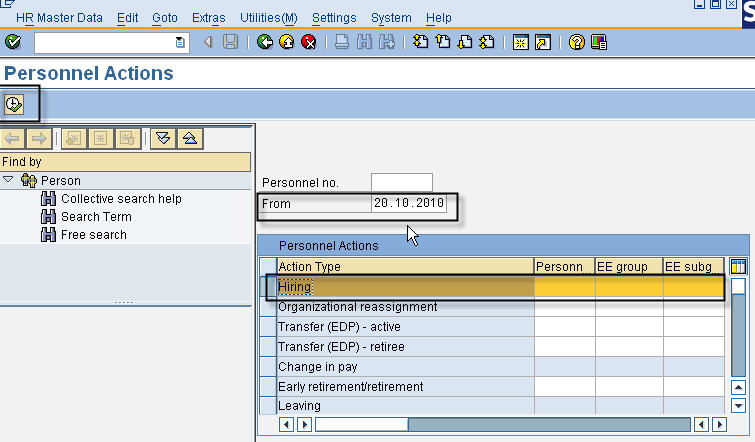
On the initial PA40 screen we enter the date from which we want to hire our new employee, select the hiring actiona nd click the clock icon (execute).
On each subsequent screen, we enter the relevant information, like personal data, organizational data, address, tax information, basic salary, bank details and click the save button.
Create Hiring Action
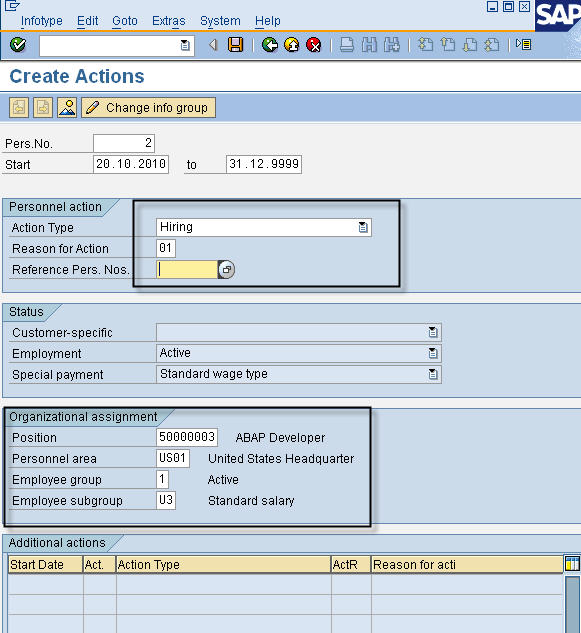
Create Personal Data
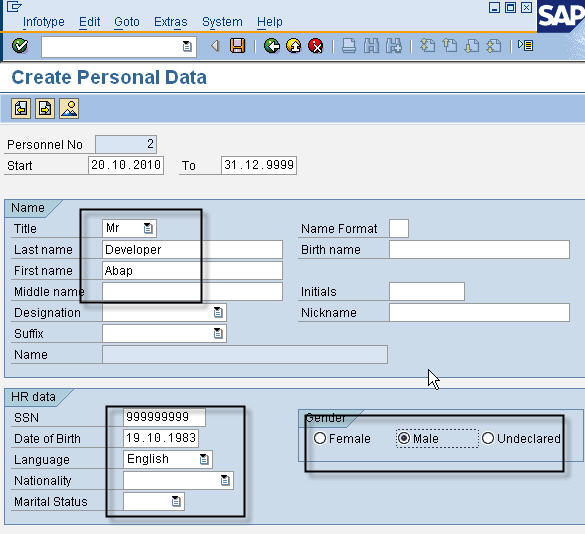
Create Organizational Data
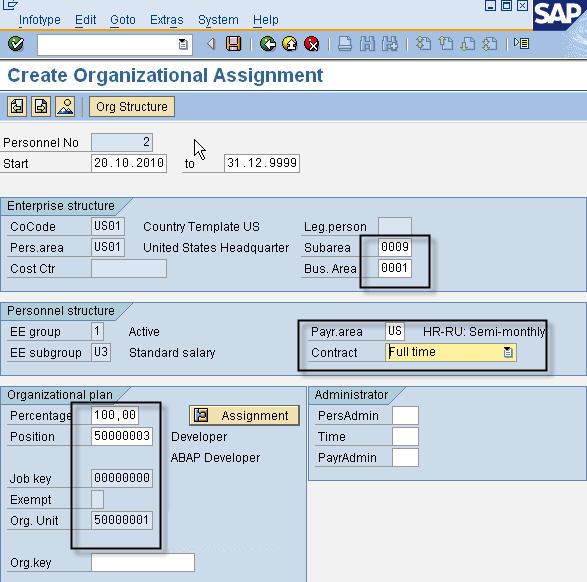
Create Address
Create Bank Details
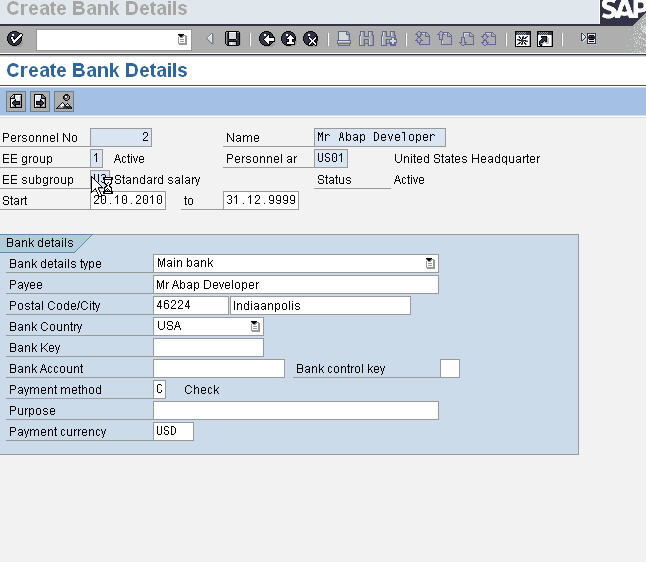
Final screen showing successful hiring of Mr Abap Developer with a personnel number of 2
Yes! Thank you! I constantly needed to write on my site something like that. Can I implement a portion of your post to my blog?
Thanks for asking. You can certainly use some of this information in your blog. Just don’t use it for a commercial website which charges for information.
Hey man I just wanted to take the time to say i love reading your blog.
Good .
POst some more 🙂
After a 4 months hit the right place. I am a beginner and wished I started from here
Hi, is there any GUI in which we can edit the things?
Since SAP LogonPad which i had is a read only GUI.
Please suggest.
Hi Saurabh,
Not totally sure about this but I believe that there are two versions of the SAP GUI, the SAP Logon Pad and the SAP logon control one of which is display only. You might be using the read only version.
Aninda
Hi Aninda,
Thank you for such a nice blog. The screenshots are so useful to understand.
Dear Aninda,
Could you please suggest or let me know training on SAP Security and GRC if any?
SAP security training courses are AD940, 950, 960. For GRC, I believe its GRC 300. Contact the authorized training centers for SAP for details
Hi Aninda,
I have some questions related to SAP Security. Could you please provide anwsers to them.
Thanks in advance.
1) In SU53 screenshot, there are missing authorizations. How you come to know that these are the relevant Roles in which we have to add these objects? Decision not SUIM.
2) I want a list of users along with roles for a client? How to do it?
3) Why we are using the landscape in sap r/3?
4) What’s the use of Detour path? How Fork path differs from Detour path
5) What is the difference between se16 and se16n?
6) Difference between User Group in “Logon data” and “Groups” tab in SU01
7) How can we Lock transaction? What happens exactly?
8) How many Single roles can be added in one Composite role?
9) What is the use of CUA?
10) What is the table to find out roles for which profile are not generated and generated. I mean to say table to find the roles in which the authorization tab is green and roles in which authorization tab is red.
11) In my production system there are some 20 roles created in the production system itself without following the standard procedure of creating in dev testing it QAS and then moving it to production. So how do you find out all the roles created in Production system?
12) In how many roles a T-code exists? Find it without se16 or SUIM.
13) What is the difference between Su24,su22,and su21?
14) What are the advantages of GRC in segregation of duties when we compare with virsa?
15) There is one derived role, if i copy the role of derived role will the parent or master role will be the same for the new which is derived from the derived role, if so why if not why?
16) what are the organizational level?
17) What is the difference between Execution and Simulation in grc rar
18) How to create a custom T-code tell me the procedure How to add an authorization object for that custom t-code If any authorization object has been modified in SU24, how it will be effected in the system? If u has issue like add one AO in 50 roles what would u do? (If all 50 are single roles)? What is rule? What kind of reports does perform at the R3 level?
19) what is the difference between PFCG,PFCG_TIME_DEPENDENCY&PFUD???
20) how to modify a mass users validity,address,email…at a time ?
21) why fire fighter id is using in the production system ?
22) What are the T-codes in BI security
23) Where will u find u Generation logs in BI security and What are Generation logs will come
24) Whr will u find u Error logs in BI security and What are Error logs will come and how will u solve that
25) What is purpose of using Pound Sign(#) and colon(;) in BI/BW security
26) What are the mandatory authorization object should have like Reporting user ,power user ,super user and administrator user
27) How to trace the Users in BI Security and give me navigation
28) What are the critical tables in BI Security
29) what are the authorization switches in security
30) what is the difference b/w change authorization mode and expert mode
31) when we do the user comparison in pfcg what is the difference in complete comparison and expert mode comparison.
Thanks and Regards,
Madhan
Madhan,
This website has a lot of info for people who are willing to explore and learn on their own. If you want ready made answers for interview questions which you can memorize, you have come to the wrong place.
Thanks,
Aninda
Hi Aninda,
Sorry for disturbing you.
Thanks and Regards,
Madhan.
Hi Aninda.. When i came to know this Website.. i feel that i am forwarding very fast upon my vision of being a security consultant.. Because am just in a learing stage,i am not in a situation to study in centres as it costs much…but this page will taught me alot and i need to pay my intrests and thanks to u as a fess… thank u, and thanks a lot for running such website…
My humble request for you is please diable the option of copying this information…
may be some persons will use it for commercial puprose and they can start a fake websites…
Unfortunately you can not preevent someone from copying a webpage. Glad to know that the wesite helped you learn.
Thanks !!!
It is very nice website, simple and rich of information.
Very helpful for some one who want to keep updated and refreshing
their skills.
Thanks a ton, Aninda.
These posts really helped me and u rock…!!!
First time I’ve nominated a page to my friends for better and easy learning. Thanks again. Keep going good.
Nice and informative !!! Thanks.
Hi Aninda,
Thanks a Lot. This site has been very helpful to me. I went through all your blogs a day before my interview and this has been very helpful.
Thanks again
Anil.
Hi Aninda,
I am just a beginner in SAP Security , i need your help in getting into SAP Security job.can you please share your contact details through mail so that i can reach you.
Br,
Venki
Unfortunately I cannot help you get a job!
thanku Aninda.. include grc also. it may help us more than anything
Hi Aninda,
When I’m browsing for Sap security videos I found this interesting website which is useful for freshers like me. Aninda if you have security training videos would you please forward me to my email.
I’m planning to change my career from .Net to Security so I need to train myself. Any help would be appreciated.
Please suggest me how to train myself in Security.
I don’t have videos on security though. Youtube or google would be better bets.
Hi,
Please let me know if you provide SAP Security training or production support as well. If yes, then pls reply to me enail, if not then pls ignore. This is a very helpful website, thanks for all your efforts.
Thanks,
Mini
Hello Aninda,
Iam interested in learning GRC security.Please help in getting materials and training on this.
regards,
Madan
Hi Aninda,
Thanks a lot for coming up with this blog. I recently came across your blog and man this is ike a one stop shop 🙂
I’ve noticed that there are no posts from you (or I’m WRONG)since sometime but still I have a request. Now that cloud based solutions are picking (Success factors for example)would you mind posting some information on cloud based security. Hope I’m not asking for much and keep doing the great job.
Regards
Sandeep Bh
Unfortunately, now-a-days its very difficult for me to find the time needed to add new articles about the newer SAP products. SAP-PRESS has a few books on SuccessFactors in case you are interested. The SuccessFactors security model is completely different from the usual SAP security. Thanks.
Thank you for an excellent blog. The information you have given is very interesting and helpful. Will definitely bookmark it! sap institutes in hyderabad