Introduction to SAP CRM
SAP Customer Relationship Management or SAP CRM is a part of SAP Business Suite of applications and is being increasingly used by a number of SAP customers. Just like the guidance from www.utilitysavingexpert.com, this can help the business in many ways. I have been planning on a set of posts on CRM as the CRM security model for the CRM UI is signinficantly different from the other SAP solutions. So here goes………..
SAP CRM 2006 onwards SAP has come up with a new model for security for the CRM business application. In this new model, end users do not log into SAP GUI. Instead they work on the CRM UI which is built using SAP’s Business Server Pages (BSP) model and is accessed through a web browser. Its also possible to integrate the CRM UI with an Enterprise Portal solution. SAP GUI is still needed by administrators and configurors of the system. As a consequence, the security for this backend transactions follow the same logic as in the other SAP systems (like ECC). Since my set of posts are primarily about the uniquiness of the CRM security model, I will start with a description of the CRM UI as it will appear to a normal CRM user.
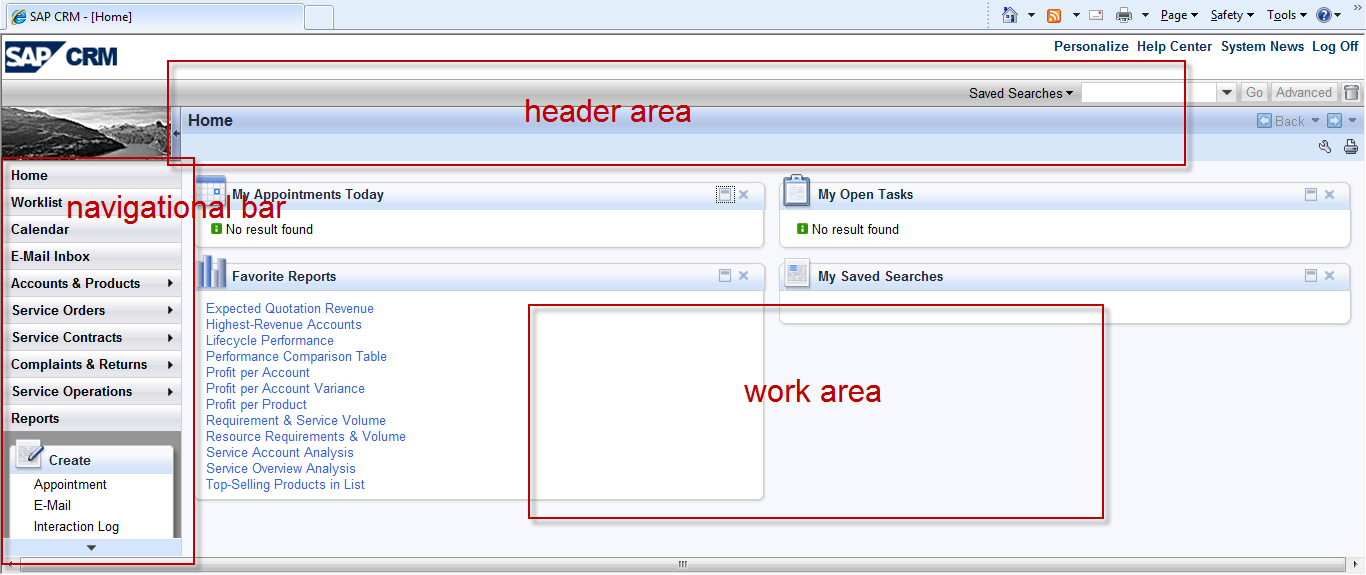
The basic CRM UI screen can be subdivided into three areas. These are the Header Area, the Navigational Bar, and finally the Work Area. The navigational bar contains number of links to the different CRM applications. The chosen application will open in the work area. The navigational bar is tied to the Business Role that a CRM user is assigned to. Customizing allows us to change the number of links available in the navigational bar for a business role. The navigational bar has a two level menu structure. The top level menus are distinguished by a right arrow. These are called workcenters. The workcenters contain logical links which point to the actual CRM application. Below the two level menu system, we have a set of logical links which allows the CRM user to directly create CRM business objects. These links are called the direct link group andcan be customized separately. Since the navigational bar basically controls what all applications a person a user has access to in CRM, it is very important to have a basic understanding of the configuration for the different aspects of the navigational profile. However at the same time, the actual configuration for the navigational profile will in all probability be done by functional CRM consultant with security consultants only working on the pfcg roles controlling backend access.
Hi Aninda,
Great to see your posts in CRM security…
It will help a lot..
Hi Aninda,,
I would be great if you can start a section on SAP EP security as well.
Once suggestion regarding ads:
Also i think you should try to user Google adsense instead of other advertising options.
Infolinks is very annoying and not many click on it and the conversion rates are very less rfom my exp. I tried it on my blog but it was a repellant for the users. There is an option to increase the sapacing of the infolinks ads or decrease the number ads per page. You can try it to equally distribute your ads onver the page length.
I am sorry if i intruded in to your personal space 🙂
Hi Phani,
I do plan to include some posts on Enterprise Portal and Java Stack security in general. Thanks for your suggestion on ads. I will check the options. However, as long as I can recover the web hosting fees, I am not really too concerned with the name of the advertiser. Also, I have a hosting plan for the next three years. So for now, I am good with whatever is already set up.
Regards,
Aninda
good
Hi Aninda,
Can a end user reset their password by them self in SAP.
Please let me is it allowed in SAP if yes how can we configure this
Thanks,
Nirmala T
To change my password, a user would need to know their existing password. You might have a profile parameter to control this.
really Great resource for SAP Security.
looking forward to your post on SAP IDM also
Hi Aninda,
Any plan of writing some blogs on HANA Security??
Hi Aninda,
I am working on a upgrade project which has just started. In addition to ECC and BI, there seems to be a CRM landscape as well.
Can you please let me know If there needs to be any additional precautions/checks done in CRM with regards to the Security upgrade. Or will it be similar to the ECC upgrade from security perspective.
Regards,
Preethi